Information & Cyber Security Consultancy for your Business
Securing your business with tailored cybersecurity strategies and expert support every step of the way.
Incident Response Planning
Comprehensive planning and testing for effective incident response plans tailored to your needs.
Testing and Validation
The effectiveness of any plan relies on its execution. This service tests preparedness through realistic simulations and drills, evaluating the plan's efficacy, team capabilities, and technical controls. Detailed feedback and recommendations help refine processes, improve coordination, and ensure a team is confident and ready for cyber incidents.
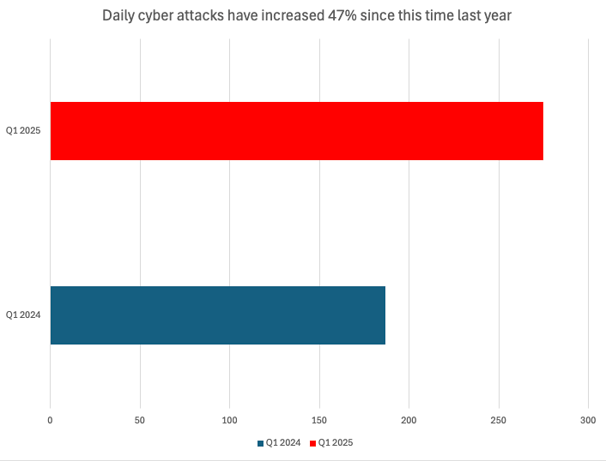
Planning
Effectively managing cyber incidents requires a robust framework. This service helps businesses develop tailored strategies, define roles, and establish communication protocols, providing a clear roadmap from detection to recovery. This comprehensive planning minimises downtime, reduces financial losses, and protects an organisation's reputation during an attack.
Based on the UK Cyber Security Breaches Survey 2025 (which covers a period including parts of 2024 and early 2025):
Only 23% of businesses overall have a formal cybersecurity incident management plan in place.
This means that 77% of businesses did not have a formal incident response plan when a cyber attack occurred, or at least at the time of the survey.
IT Policy Solutions
Expert services for creating IT policies that meet industry standards and frameworks effectively.
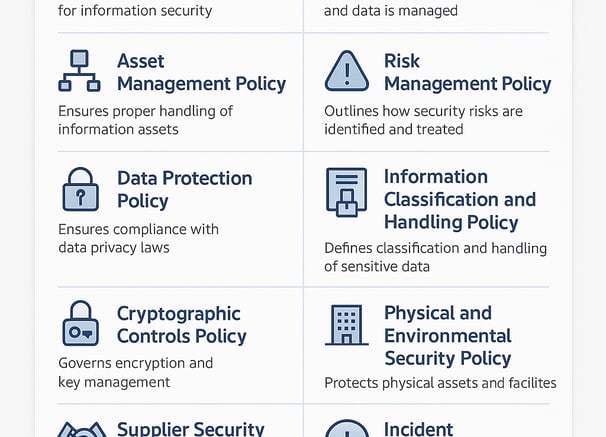

Bespoke IT Policy Development
Crafting strong IT policies aligned with ISO 27001 and NIST is vital for cybersecurity. This service develops custom-tailored IT policies that fit your organisation's unique needs, ensuring compliance, reducing vulnerabilities, and fostering a security-first culture.
ISO 27001 Policy Templates
Crafting strong IT policies aligned with ISO 27001 and NIST is vital for cybersecurity. This service develops custom-tailored IT policies that fit your organisation's unique needs, ensuring compliance, reducing vulnerabilities, and fostering a security-first culture.
Gap Analysis
Leveraging an extensive IT infrastructure security background, Stride Security provides exceptionally thorough gap analyses. This involves a deep dive into existing security controls across diverse IT environments, meticulously comparing them against industry best practices and recognised frameworks.


Thorough Analysis
Expert analysis of security controls and hands-on experience means no stone is left unturned.
Actionable Roadmap
This in-depth scrutiny pinpoints subtle vulnerabilities, offering a clear, actionable roadmap to strengthen your organisation's foundational security posture. identifying gaps is also an excellent way to prepare to undertake any cyber strategy projects.
Cyber Security Strategy
Expert strategies for comprehensive cyber security, including writing and feedback services.
Tailored Cybersecurity Writing Services
Stride Security's cyber security writing services are meticulously tailored. They are built upon a deep understanding of each client's unique landscape, derived from detailed gap analyses.


Stride Security's cyber security writing services are meticulously tailored. They are built upon a deep understanding of each client's unique landscape, derived from detailed gap analyses.
Custom & Actionable Strategies
© Copyright Stride Security 2025 All Rights Reserved | Privacy Policy | Contact Us
